Active Directory
Introduction
Active Directory enables centralized, secure management of an entire network, which might span a building, a city, or multiple locations throughout the world.

https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc780036(v=ws.10)
Components
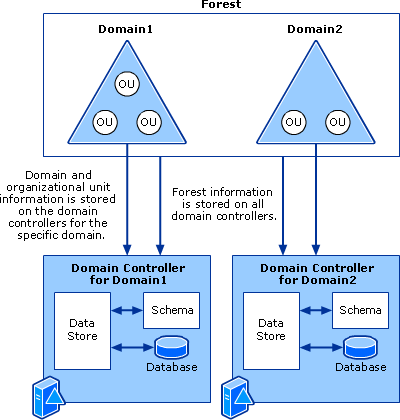
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc759186(v%3dws.10)
| Component | Description |
|---|---|
| Organizational Units |
|
| Domains |
|
| Domain Trees |
|
| Forests |
|
| Site Objects |
|
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc759073(v%3dws.10)
- Schema - Defines objects and attributes
- Query and index mechanism - Ability to search and publish objects and properties
- Global Catalog - Contains info about every object in directory
- Replication Service - Distributes information across domain controller
Detect Firewall Blocking AD
PortQryUI - http://www.microsoft.com/download/en/details.aspx?id=24009 * Run the “Domains & Trusts” option between DCs, or between DCs and any machine * “NOTLISTENING,” 0x00000001, and 0x00000002, that means there is a port block * Can ignore UDP 389 and UDP 88 messages * TCP 42 errors, that just means WINS is not running on the target server
https://blogs.msmvps.com/acefekay/2011/11/01/active-directory-firewall-ports-let-s-try-to-make-this-simple/
Implementing Least Privilege Model
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/implementing-least-privilege-administrative-models
Scanning
pingcastle.exe --healthcheck --server <DOMAIN_CONTROLLER_IP> --user <USERNAME> --password <PASSWORD> --advanced-live --nullsession
- Automating AD Enumeration (Bloodhound, PowerUp, Responder, CrackMapExec): https://medium.com/bugbountywriteup/automating-ad-enumeration-with-frameworks-f8c7449563be
Tools
ldapsearch
- Query the Domain Controller for Active Directory
- UserAccountControl attributes of active accounts
- Other specific configurations
- Possible UserAccountControl values: https://support.microsoft.com/en-gb/help/305144/how-to-use-the-useraccountcontrol-flags-to-manipulate-user-account-pro
Active users (2 == disabled account status)
ldapsearch -x -h $ip -p 389 -D 'SVC_TGS' -w $password -b "dc=active,dc=htb" -s sub "(&(objectCategory=person)(objectClass=user)(!(useraccountcontrol:1.2.840.113556.1.4.803:=2)))" samaccountname
Impacket’s GetADUsers.py
- Enumerate domain user accounts
GetADUsers.py -all active.htb/svc_tgs -dc-ip $ip
Attack Patterns
- Wagging the Dog: Abusing Resource-Based Constrained Delegation to Attack Active Directory: https://shenaniganslabs.io/2019/01/28/Wagging-the-Dog.html
- Escalating privileges with ACLs in Active Directory: https://blog.fox-it.com/2018/04/26/escalating-privileges-with-acls-in-active-directory/
Defense
- Active Directory Core Security Principles & Best Practices: https://ernw.de/download/AD_Summit_2018/01_AD_Summit_CoreSecPrinciples_fk_hw_v.1.2_signed.pdf
- Active Directory Kill Chain Attack & Defense: https://github.com/infosecn1nja/AD-Attack-Defense
- Microsoft-Blue-Forest: https://github.com/rootsecdev/Microsoft-Blue-Forest
- Welcome to building your first domain controller!: https://github.com/rootsecdev/Microsoft-Blue-Forest/blob/master/FirstDomainControllerInstall.md
- Pwn and Defend - Active Directory Domain Enumeration: https://www.youtube.com/watch?v=YxeXfHkHAUI&feature=youtu.be